ASSESS IMPACT & CREATE AN ASSURANCE MAP
The audit impact assessment and assurance map are interdependent—and the best possible starting point for your combined assurance journey. An impact assessment begins with a critical look at the current or “as is” state of your organization. As you review your current state, you build out your assurance map with your findings. You can’t really do one without the other. The map, then, will reveal any overlaps and gaps, and provide insight into the resources, time, and costs you might require during your implementation. Looking at an assurance map example will give you a better idea of what we’re talking about. The Institute of Chartered Accountants of England and Wales (ICAEW) has an excellent template.
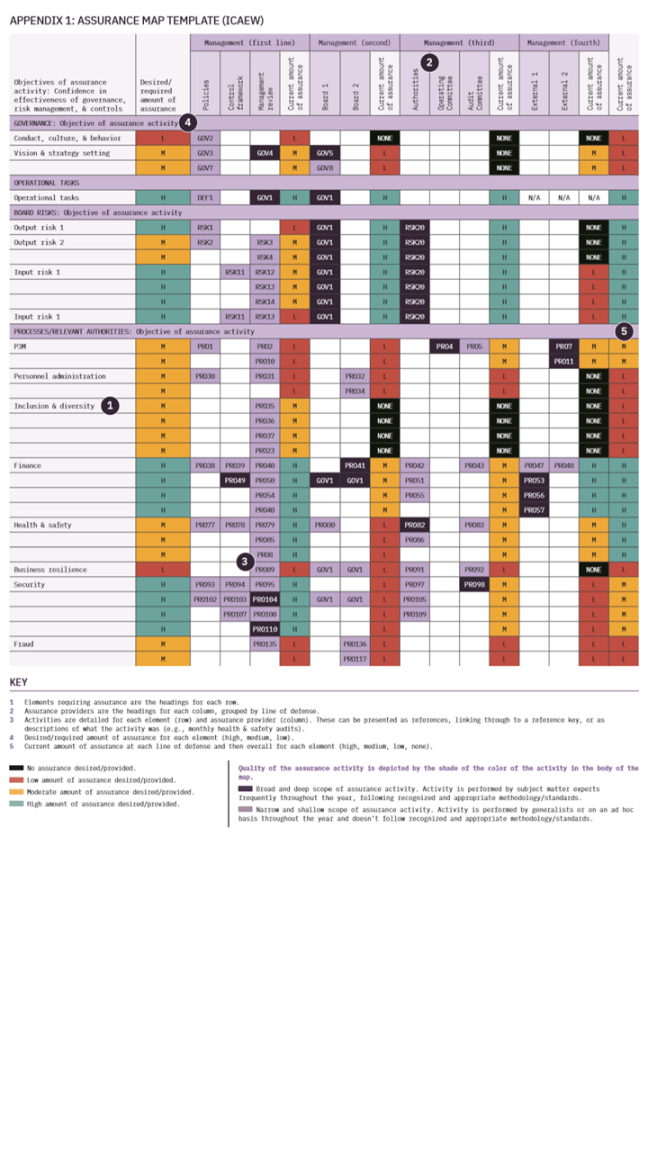
The ICAEW has also provided a guide to building a sound assurance map. The institute suggests you take the following steps:
- Identify your sponsor (the main user/senior staff member who will act as a champion).
- Determine your scope (identify elements that need assurance, like operational/ business processes, board-level risks, governance, and compliance).
- Assess the required amount of assurance for each element (understand what the required or desired amount of assurance is across aspects of the organization).
- Identify and list your assurance providers in each line of defense (e.g., audit committee or risk committee in the third line).
- Identify your assurance activities (compile and review relevant documentation, select and interview area leads, collate and assess assurance provider information).
- Reassess your scope (revisit and update your map scope, based on the information you have gathered/evaluated to date).
- Assess the quality of your assurance activities (look at breadth and depth of scope, assurance provider competence, how often activities are reviewed, and the strengths/quality of assurance delivered by each line of defense).
- Assess the aggregate actual amount of assurance for each element (the total amount of assurance needs to be assessed, collating all the assurance being provided by each line of defense).
- Identify the gaps and overlaps in assurance for each element (compare the actual amount of assurance with the desired amount to determine if there are gaps or overlaps).
- Determine your course of action (make recommendations for the actions to be taken/activities to be performed moving forward).
Just based on the steps above, you could understand how your desired state evolves by the time you reach step 10. Ideally, by this point, gaps and overlaps have been eliminated. But the steps we just reviewed don’t cover the frequency of each review and they don’t determine costs. So we’ve decided to add a few more steps to round it out:
- Assess the frequency of each assurance activity.
- Identify total cost for all the assurance activities in the current state.
- Identify the total cost for combined assurance (i.e., when gaps and overlaps have been addressed, and any consequent benefits or cost savings).
DEFINE THE RISKS OF IMPLEMENTATION
Implementing combined assurance is a project, and like any project, there’s a chance it can go sideways and fail, losing you both time and money. So, just like anything else in business, you need to take a risk-based approach. As part of this stage, you’ll want to clearly define the risks of implementing a combined assurance program, and add these risks, along with a mitigation plan and the expected benefits, to your tool kit. As long as the projected benefits of the project outweigh the residual risks and costs, the implementation program is worth pursuing. You’ll need to be able to demonstrate that a little further down the process.
DEFINE RESOURCES & DELIVERABLES
Whoever will own the project of implementing combined assurance will no doubt need dedicated resources in order to execute. So, who do we bring in? On first thought, the internal audit team looks best suited to drive the program forward. But, during the implementation phase, you’ll actually want a cross-functional team of people from internal control, risk, and IT, to work alongside internal audit. So, when you’re considering resourcing, think about each and every team this project touches. Now you know who’s going to do the work, you’ll want to define what they’re doing (key milestones) and when it will be delivered (time frame). And finally, define the actual benefits, as well as the tangible deliverables/outcomes of implementing combined assurance. (The table below provides some examples, but each organization will be unique.)

RAISE AWARENESS & GET MANAGEMENT COMMITMENT
Congratulations! You’re now armed with a fancy color-coded impact assessment, and a full list of risks, resources, and deliverables. The next step is to clearly communicate and share the driving factors behind your combined assurance initiative. If you want them to support and champion your efforts, top management will need to be able to quickly take in and understand the rationale behind your desire for combined assurance. Critical output: You’ll want to create a presentation kit of sorts, including the assurance map, lists of risks, resources, and deliverables, a cost/benefit analysis, and any supporting research or frameworks (e.g., the King IV Report, FRC Corporate Governance Code, available industry analysis, and case studies). Chances are, you’ll be presenting this concept more than once, so if you can gather and organize everything in a single spot, that will save a lot of headaches down the track.
ASSIGN ACCOUNTABILITY
When we ask the question, “Who owns the implementation of combined assurance?”, we need to consider two main things:
- Who would be most impacted if combined assurance were implemented?
- Who would be senior enough to work across teams to actually get the job done?
It’s evident that a board/C-level executive should lead the project. This project will be spanning multiple departments and require buy-in from many people—so you need someone who can influence and convince. Therefore, we feel that the chief audit executive (CAE) and/or the chief revenue officer (CRO) should be accountable for implementing combined assurance. The CAE literally stands at the intersection of internal and external assurance. Where reliance is placed on the work of others, the CAE is still accountable and responsible for ensuring adequate support for conclusions and opinions reached by the internal audit activity. And the CRO is taking a more active interest in assurance maps as they become increasingly more risk-focused. The Institute of Internal Auditors (IIA), Standard 2050, also assigns accountability to the CAE, stating: “The chief audit executive should share information and coordinate activities with other internal and external assurance providers and consulting services to ensure proper coverage and minimize duplication of effort.” So, not only is the CAE at the intersection of assurance, they’re also directing traffic—exactly the combination we need to drive implementation.
Envisioning the solution
You’ve summarized the current/“as is” state in your assurance map. Now it’s time to move into a future state of mind and envision your desired state. What does your combined assurance solution look like? And, more critically, how will you create it? This stage involves more assessment work. Only now you’ll be digging into the maturity levels of your organization’s risk management and internal audit process, as well as the capabilities and maturity of your Three Lines of Defense. This is where you answer the questions, “What do I want?”, and “Is it even feasible?” Some make-or-break capability factors for implementing combined assurance include:
- Corporate risk culture Risk culture and risk appetite shape an organization’s decision-making, and that culture is reflected at every level. Organizations who are more risk-averse tend to be unwilling to make quick decisions without evidence and data. On the other hand, risk-tolerant organizations take more risks, make rapid decisions, and pivot quickly, often without performing due diligence. How will your risk culture shape your combined assurance program?
- Risk management awareness If employees don’t know—and don’t prioritize— how risk can and should be managed in your organization, your implementation program will fail. Assurance is very closely tied to risk, so it’s important to communicate constantly and make people aware that risk at every level must be adequately managed.
- Risk management processes We just stated that risk and assurance are tightly coupled, so it makes sense that the more mature your risk management processes are, the easier it will be to implement combined assurance. Mature risk management means you’ve got processes defined, documented, running, and refined. For the lucky few who have all of these things, you’re going to have a much easier time compared to those who don’t.
- Risk & controls taxonomy Without question, you will require a common risk and compliance language. We can’t have people making up names for tools, referring to processes in different ways, or worst of all, reporting on totally random KPIs. The result of combined assurance should be “one language, one voice, one view” of the risks and issues across the organization.
- System & process integrations An integrated system where there is one set of risks and one set of controls is key to delivering effective combined assurance. This includes: Risk registers across the organization, Controls across the organization Issues and audit findings, Reporting.
- Technology use Without dedicated software technology, it’s extremely difficult to provide a sustainable risk management system with sound processes, a single taxonomy, and integrated risks and controls. How technology is used in your organization will determine the sustainability of combined assurance. (If you already have a risk management and controls platform that has these integration capabilities, implementation will be easier.)
- Using assurance maps as monitoring tools Assurance maps aren’t just for envisioning end-states; they’re also critical monitoring tools that can feed data into your dashboard. They can inform your combined assurance dashboard, to help report on progress.
- Continuous improvement mechanisms A mature program will always have improvement mechanisms and feedback loops to incorporate user and stakeholder feedback. A lack of this feedback mechanism will impact the continued effectiveness of combined assurance.
We now assess the maturity of these factors (plus any others that you find relevant) and rank them on a scale of 1-4:
- Level 1: Not achieved (0-15% of target).
- Level 2: Partially achieved (15-50%).
- Level 3: Largely achieved (50-85%).
- Level 4: Achieved (85-100%).
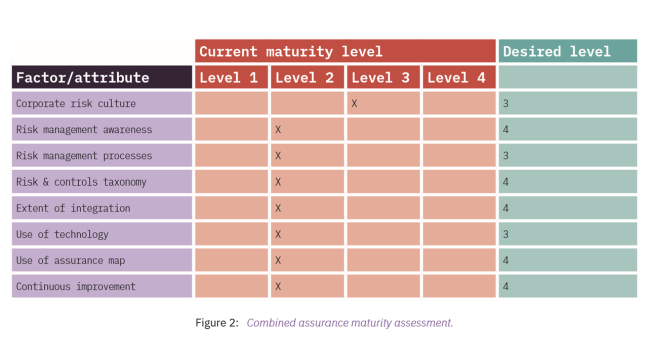
This rating scale is based on the ISO/IEC 15504 that assigns a rating to the degree each objective (process capability) is achieved. An example of a combined assurance capability maturity assessment can be seen in Figure 2.
GAP ANALYSIS
Once the desired levels for all of the factors are agreed on and endorsed by senior management, the next step is to undertake a gap analysis. The example in Figure 2 shows that the current overall maturity level is a 2 and the desired level is a 3 or 4 for each factor. The gap for each factor needs to be analyzed for the activities and resources required to bridge it. Then you can envision the solution and create a roadmap to bridge the gap(s).
SOLUTION VISION & ROADMAP
An example solution vision and roadmap could be:
- We will use the same terminology and language for risk in all parts of the organization, and establish a single risk dictionary as a central repository.
- All risks will be categorized according to severity and criticality and be mapped to assurance providers to ensure that no risk is assessed by more than one provider.
- A rolling assurance plan will be prepared to ensure that risks are appropriately prioritized and reviewed at least once every two years.
- An integrated, real-time report will be available on demand to show the status, frequency, and coverage of assurance activities.
- The integrated report/assurance map will be shared with the board, audit committee, and risk committee regularly (e.g., quarterly or half-yearly).
- To enable these capabilities, risk capture, storage, and reporting will be automated using an integrated software platform.
Figure 3 shows an example roadmap to achieve your desired maturity level.

Click here to access Galvanize’s Risk Manangement White Paper