Where are organizations heading ?
“Data Driven GRC” represents a consolidation of methodologies, both functional and technological, that dramatically enhance the opportunity to address emerging risk landscapes and, in turn, maximizing the reliability of organizational performance. This paper examines the key opportunities to leverage change—both from a risk and an organizational performance management perspective—to build integrated, data-driven GRC processes that optimize the value of audit and risk management activities, as well as the investments in supporting tools and techniques.
Functional Stakeholders of GRC Processes and Technology
The Institute of Internal Auditors’ (IIA) “Three Lines of Defense in Effective Risk Management and Control” model specifically addresses the “who and what” of risk management and control. It distinguishes and describes three role- and responsibility-driven functions :
- Those that own and manage risks (management – the “first line”)
- Those that oversee risks (risk, compliance, financial controls, IT – the “second line”)
- Those functions that provide independent assurance over risks (internal audit – the “third line”)
The overarching context of these three lines acknowledges the broader role of organizational governance and governing bodies.
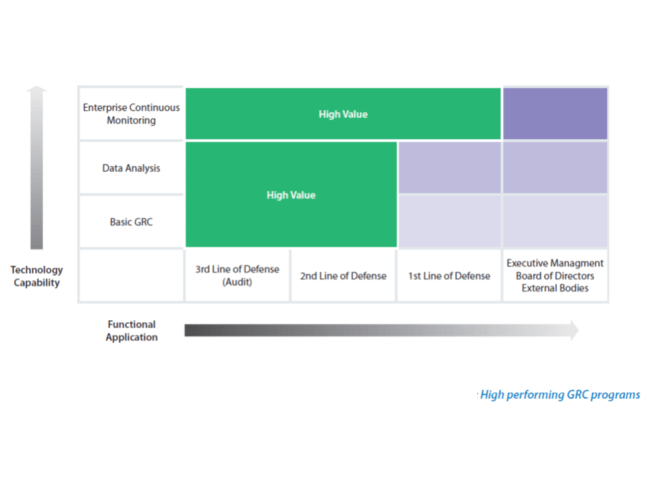
Technology Deficiencies in the Three Lines of Defense
Since the emergence of Sarbanes-Oxley, the use of technology in risk and control related processes has truly started to take meaningful shape in many organizations. However, when looking across the risk and control oriented functions in most organizations, technology is still typically used on a departmental or point solution basis.
Third Line (internal audit) use of risk & control technology
For the past decade, surveys of internal auditors have consistently identified the more effective use of technology as among the most pressing issues facing the profession. Specifically, the responses to the surveys also referred to the need for increased use of technology for audit analysis, fraud detection, and continuous auditing. Other surveys also highlight a shortage of sufficient technology and data analysis skills within audit departments.
Much of the driving force for improving the use of technology is based on the desire to make the audit process itself more efficient and more effective, as well as to deliver more tangible value to the rest of the organization.
During the past decade, the role of the internal audit function itself has changed considerably. Internal audit’s traditional focus on cyclical audits and testing internal controls is evolving into one in which internal audit is expected to assess and report on the effectiveness of management’s processes to address risk overall. This often includes providing guidance and consultation to the business on best practices for managing risk and compliance within business process areas and maintaining effective control systems. The use of technology is an increasingly critical component of these best practices and in some cases internal audit is able to champion the implementation of high-impact, high-value technology within the business’s risk management and compliance processes, based on their own experience in using technology for assurance purposes.
There is considerable variation in the extent to which internal audit departments leverage technology. However it is certainly fair to say that for audit to be truly valuable and relevant within the context of organizational strategy, a significant improvement is required across the board. Internal audit as a profession simply is not moving forward at the pace of technology.
Some specific statistics from recent research reveals:
- Only approximately 40% of internal audit departments use audit and documentation management systems from specialized vendors. The remainder use disorganized tools and processes, typically based on Microsoft Office® & shared folders.
- Audit programs for specific business process areas and industries are usually developed through a combination of previously used programs and those shared on various audit-related websites. This approach does not address organization-specific risk.
- Next generation testing techniques, especially data analytics, are overwhelmingly underutilized.
Second Line (risk, compliance, financial controls, IT) use of risk & control technology
Outside of audit, in other areas of risk and compliance, some organizations have acquired specialized departmental software, but the majority use only basic Office tools to maintain inventories of risks, document controls and perform risk assessments. In larger enterprises, it is not unusual to have a variety of different technologies and approaches applied in different operational entities or in different functional areas. This approach is usually more costly and less effective than one based on a common platform. Effective testing methods using technology are usually unavailable or left unconsidered.
In fact, second line of defense functions often rely heavily on inquiry-based methods such as surveying, which are proven ineffective at identifying the actual manifestations of risk in the organization. If analytical software is used in the business for investigations or monitoring transactions, it in many cases involves standard query tools or some form of generic business intelligence (BI) technology. Although good for providing summary level information or high-level trends, BI tools struggle to show the root cause of problems. And while they may have certain capabilities to prevent fraud and errors from occurring, or to flag exceptions, they are not sufficient to effectively trap the typical problem transactions that occur.
First Line (management) use of risk & control technology
While in some cases, first line management have access to better technology for use on specific pain point areas (e.g., continuous transaction monitoring technology used within finance departments), there is a common tendency for management to place far too much reliance on core business systems for effective control. While the large ERP and other system vendors seem to have extensive capabilities for preventing control deficiencies, the reality is that these are extremely extensive and complex systems and internal controls are usually the afterthought of those implementing them, not a core focus. For example, in many cases certain control settings are turned off to enable the ERP system to run more efficiently.
An integrated and collaborative approach to managing risks and monitoring controls in collaboration with the second and third lines of defense, using a common, independent methodology and technology platform, typically proves the most effective in accomplishing management’s key risk mitigation strategies.